Everything you need to know about the recent ransomware attacks

A few minutes every morning is all you need.
Stay up to date on the world's Headlines and Human Stories. It's fun, it's factual, it's fluff-free.
Well, after months of ransomware attacks and warnings to the White House, it seems like the big one has finally dropped.
- Well, after months of ransomware attacks and warnings to the White House, it seems like the big one has finally dropped.
- Kaseya, an IT solutions developer for thousands of businesses, announced last Friday that it had become the latest victim of a ransomware attack.
Who is Kaseya?
- Kaseya’s international headquarters is located in Dublin, Ireland, but the company operates and services companies across 10 countries.
- The company provides IT solutions for MSPs or Managed Service Providers, which are companies that provide businesses with specialized tech solutions.
- These services can be anything from customer service solutions to data analytics, and many modern businesses require the use of MSPs in order to conduct day-to-day operations.
- One of these services that Kaseya provides is called the Virtual System/Server Administrator (VSA), and it is a software used by Kaseya customers to monitor and manage their tech infrastructure through an automated system.
- When Kaseya pushed out one of their most recent updates, it came with a little bug attached to it that gave cyberterrorist group REvil direct access to some of Kaseya’s customers’ systems.
How did the attack affect thousands of businesses?
- If REvil would have only gotten access to some small businesses, the damage would have been minimal, but some of the companies that REvil gained access to were MSPs.
- By gaining access to Kaseya, REvil gained access to other companies they provided services for, but these companies also service other companies.
- Think of all this like a tree with Kaseya serving as the trunk of the tree. As the trunk extends upward, the tree begins to split into multiple branches.
- Let’s say REvil was only able to get access to a single branch on the trunk, but that branch had hundreds of limbs on it as well.
- During this process, it is currently speculated that 1,500 small to medium-sized companies were affected by the ransomware attack.
How did Kaseya react to the attack?
- On July 2, Kaseya chief executive officer Fred Voccola, announced “a potential attack against the VSA that has been limited to a small number of on-premise customers."
- During that announcement, Voccola warned clients to shut down their access to VSA immediately, and said, “It’s critical that you do this immediately because one of the first things the attacker does is shut off administrative access to the VSA."
- REvil, the organization responsible for the attack, was the same group that recently hacked a global meat production plant.
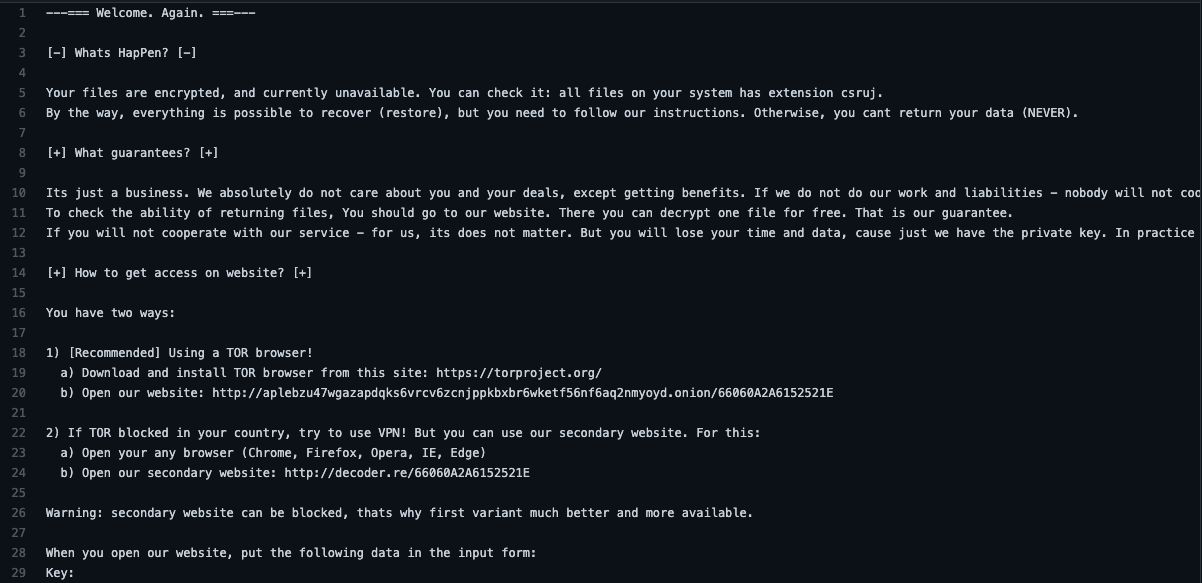
- The organization stated that they were holding files for ransom, and they expected to be paid US$70 million dollars to free the files.
- The organization also released the following statement while providing Kaseya with a single-use decryption key as proof.
- “Its just a business. We absolutely do not care about you and your deals, except getting benefits. If we do not do our work and liabilities – nobody will not cooperate with us. Its not in our interests. If you will not cooperate with our service –for us, its does not matter. But you will lose your time and data, cause just we have the private key. In practice – time is much more valuable than money."
How has law enforcement responded?
- As soon as Kaseya realized that it had been attacked, the company immediately notified law enforcement and cybersecurity agencies, including the Federal Bureau of Investigation (FBI) and US Cybersecurity and Infrastructure Security Agency (CISA).
- The two government entities have released a joint statement on the incident, and they are also encouraging customers to use a tool provided by Kaseya that will determine whether or not their systems are compromised.
- The White House released a warning to Russian President Vladimir Putin stating that the leader needed to take action or “we will take action or reserve the right to take action on our own."
What comes next?
- Kaseya has already started moving away from investigating the cause of the incident, and they are looking forward to taking preventive measures to ensure that this does not happen again. The company announced that they “will be publishing a summary of the attack and what we have done to mitigate it.”
- So far, the VSA system is still not fully operational as Kaseya has claimed to have it operational by July 6, but the company has had to push back the date to at least July 8 as they remain cautious.
- Kaseya wanted to remind all customers to continue keeping the system offline until the company can release its patch to the system.
- “All on-premises VSA Servers should continue to remain offline until further instructions from Kaseya about when it is safe to restore operations," the firm said. “A patch will be required to be installed prior to restarting the VSA."
- The Kaseya hack comes at a similar time as last week’s separate Republican National Committee (RNC) hack, which was first reported by Bloomberg. The group behind the RNC hack, however, were part of the APT 29 or otherwise known as Cozy Bear group.
- This group that has been tied to Russia’s foreign intelligence service and was also behind the SolarWinds hack.
Have a tip or story? Get in touch with our reporters at tips@themilsource.com




Comments ()